Crypto¶
Table of Contents

Intro¶
Lonero is a newly emerging cryptocurrency that aims to be the future of digital cash. The problem with current privacy coins, alt coins, and emerging cryptocurrencies relies mainly on stability, security, and an unknown future. We aim to fix many of these stability issues, be extremely decentralized, and have technology that actively supports the community. We are utilizing some of the most advanced technological protocols in order to do so. This includes our consensus protocols that support less barriers amongst ASIC vs. Non-ASIC systems, along with the Cryptonote foundation’s widely trusted ring signature protocols, multiple layers of security, and a utilization of “Proof of Work” and “Proof of Space” mining. Among the technology we are also integrating a Decentralized Autonomous Organization or DAO, bounty programs, and a mathematical proof that allows further decentralization. We believe that mining rewards shouldn’t merely be limited to hardware specifications but also to total mathematical knowledge, so we provide a fair market game to everyone involved.
Abstract¶
The components of what makes Lonero unique is split into four different parts: The HashBolt Masternode consensus, the DAO integrations, Cryptonote’s ring signature integration, and multipath layer security. In terms of the masternode consensus, we aren’t only allowing both ASIC and Non-ASIC systems to profitably mine our cryptocurrency. We are also granting large server infrastructures and x86 computer systems an easier way to mine Lonero. The DAO integration that we are doing is less of an organization and more of an integrative, curated, and regressional artificial intelligence. We set parameters that prevent spamming or abusing of the system to curate within our network and provide a non-redundant experience for our users. This allows us to be fully private, without running into compilations in our infrastructure or allow usage Lonero in cryptojacking or distributed bot nets.
We aim to be one of the industry’s first privacy coins that is institutionally compliant while still allowing a libertarian like usage. We support an open free market for our users as Lonero truly is, as stated, the future of digital cash. The utilization of cryptonote’s ring signatures, while allowing multi-path layer security creates higher technological stability among the transactional usage of our cryptocurrency. Over time, we aim to be secure enough where financial institutions and FinCEN regulated entities would allow an integration of our system amongst theirs.
Our masternode consensus known as HashBolt allows for an extremely decentralized crypto. It wouldn’t just break traditional hardware mining barriers, but components such as difficulty targets don’t solely determine technological value. Some mathematical components of our crypto can also be solved by building recursive functions for analyzing polynomial time or integrating merkle tree proofs for certain transactions. The fact that we utilize the ability for segregated witnesses and the algorithmic capabilities of what we are creating, allows for easy scalability of the network over time.
Cryptonight Integration¶
Part of our integration will be utilizing Cryptonote’s Cryptonight algorithm for our PoW hashing. Just like Bytecoin, Monero, and Digibyte, we are aiming to be on the verge of the next big cryptonote based privacy coin. While traditional usage of cryptonote’s algorithm works best on CPU cores, we aim to have driver support for all major mining methods, in terms of profitability. This includes servers, GPU mining rigs, and x86 desktop computers. Lonero also plans on having major mining integrations. This will include planned integration with P2Pool as well as further plans to expand configurations for UNOMP, Nanopool, and many Cuda drivers. The allowance of Lonero being integrated with core technologies related to open source mining pools or traditional drivers allows for mass adoption of Lonero as a highly sought after PoW/PoC based cryptocurrency.
In addition to the cryptonight integration, we are utilizing a PoC system for verifying regressional times in our blocks. As mentioned earlier, it is merely traditional hardware proof of work that allows you to develop custom mathematical solutions on your hard drive for transactional verification with minimal hardware. This can be accomplished based on the mathematical proofs we are utilizing for Lonero’s cryptocurrency. Therefore, we identify as more of a hybrid form of mining that utilizes cryptonight’s hashing system, rather than just pure cryptonight in general.

A crucial technological innovation that makes Lonero superior is our HashBolt masternode consensus. Traditional masternodes allow a form of PoW system for processing transactions under a PoS type solution. They are usually extremely costly on the added premise that you can earn a much higher amount of crypto by operating a masternode. Eventually when the network becomes so congested, a masternode’s ROI is less than the current masternode cost. We have decided to change this. We are offering a masternode type consensus for our community for free.
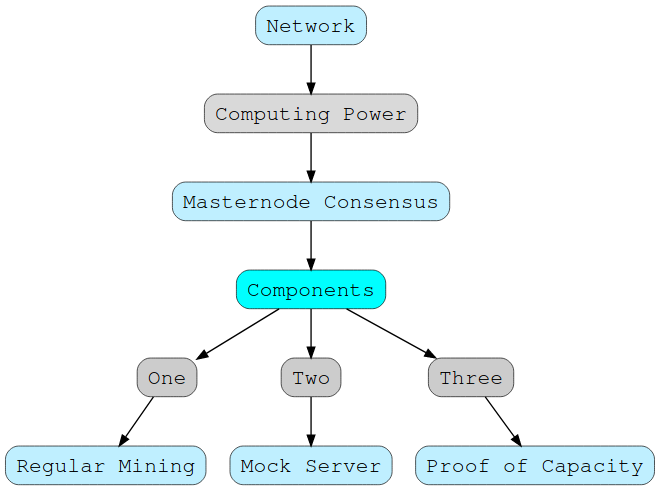
This means that not only are regular users able to mine, but we will allow numerous extensions for people to run a masternode type system for Lonero. This will grant users with superior hardware specifications or mathematical capabilities to host mining farms, verify signatures more intuitively, and allow both ASIC and Non-ASIC systems to take place in healthy competition.
The Lonero Foundation¶
The Lonero Foundation is the group behind the further development of Lonero and its community. Our goal as the Lonero Foundation is to drive the prosperous usage of Lonero (LNR) and the technological potential of cryptocurrencies. We aim to ensure that projects built on top of Lonero are beneficial for the industry and plan on making strategic partnerships for continued sustainability and growth. We will always advocate for privacy, security, and social awareness of topics that effect the industry. This includes: “Supporting a free market”, “Decentralized usage of crypto”, “Avoiding market monopolies”, “Privacy in our digital age”, and sustaining our community. We believe a free market society that encourages healthy competition is part of what could make cryptocurrency great.
Economically struggling third world countries could greatly benefit from the use of cryptocurrencies and spawn a new era of societal development. The world around us needs a free market society based off of technological advantages, opportunities, and a truly decentralized P2P system. The original goal of Bitcoin was to provide a decentralized, point to point electronic cash system free from centralization by the policies of a single entity. We believe the original Bitcoin Core still holds true to that mission, as well as many other cryptocurrencies in the market today. However, the decentralization aspect can be taken even further. The greatest issue facing other cryptocurrencies in comparison to Bitcoin is the illusion of demand without a fully perceived technological value.
Major companies in essence are using ICOs and the exchange of cryptocurrencies as a monopoly. Projects are raising hundreds of millions and reaching multi-billion-dollar market caps without a finished product or a Minimum Viable Product. This trend needs to end, as it is problematic for the continuation of a sustainable community. The Lonero Foundation also believes that it isn’t the lack of regulation that is hurting the cryptocurrency community, as much as a combination of greed and technological ignorance. With the technologies featured by Lonero, having one of the largest Initial Coin Offerings is very possible, however we find no need to do so. If the team can develop the technology and believe that it can grow purely on the basis of technological value, an ICO is meaningless.
Privacy is an extremely important topic for us. Many people in the technology industry are beginning to advocate that privacy is dead, and a critical problem is the misuse of our personal data. While it is true that people allow this misuse to some extent, many companies still go far with what they use our data for. We at the Lonero foundation aim to never collect the personal data of our users without informing them prior to doing so, as well as never using your personal data for political or monetary gain.
Transparency is important to us, and one of the values that the Lonero Foundation closely adheres to. Without transparency, it is fully difficult for a community to flourish. A proper community always flourishes with trust and a great product. Throughout our mission we aim to be one of the most transparent and community focused teams in the industry.
What are Merkle Trees?¶
Merkle trees are an important part of the transactional structure of most cryptocurrencies. Lonero’s own infrastructure will rely on a merkle tree proof but have layers of complexities integrated in it. This allows for a better integration of its current technologies. Current merkle trees utilize an infrastructure that starts with the root and creates a “leaf and tree node” for transactional hashes. What we do is integrate a merkle proof for cryptographic complexity then utilize a ring signature verification protocol for auditory proof of the transaction. All this happens while we are integrating higher capacity path wall layers for encryption and compressing the block in order to prevent the network from overloading. Since we are utilizing this protocol, we can prevent network congestion.
The allowance of transactional nodes, allows us to integrate with multipath layer security and the ring signature protocol much more efficiently. Since we are integrating PoW and PoC mining in our consensus, we can offset the network cache while still allowing for a high method of complexity for the security of Lonero’s blockchain. The best way to state it is the following:
- Start the root: (Merkle Tree’s origin for the transaction)
- Integrate the sub root (Nodes of the transactions)
- Verify the ring signatures (Before going to the next node)
- Add a layer of complexity for the hashes upon the next node
- Repeat for every transaction
Defining Cryptocurrency¶
A Cryptocurrency is a medium of exchange that integrates hash based algorithms or cryptography for more secure transactions. Most cryptocurrencies utilize peer to peer communication for decentralized networks, and have some sort of proof based algorithm for the feasibility of the network. The most common proofs are: PoW (Proof of Work), PoC (Proof of Capacity/Space), PoS (Proof of Stake), Proof of Signature, and Hybrids. Many cryptocurrencies also utilize an origin block and transactional merkle trees.
Multi-Path Layer Security¶
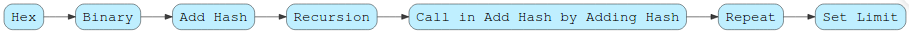
The Lonero Foundation plans on integrating multipath layer security into our network. This applies to the ring signature and the transactional nodes. The allowance of multipath layer security will keep our network stable for long term user support and growth. The security protocol is broken into a series of parts. First, one must start with the original transactional hash. Then, once the ring signatures are verified, layers of hashes are added to the complexity and difficulty target. For the next node, the same process repeats recursively. Eventually, the network keeps getting higher in security and transactional nodes are nearly impossible to crack. The better this is integrated by algorithmic means to the network, the more stable future Lonero will have as a cryptocurrency.
Later, this can inspire newer projects or cryptocurrencies, and even way more advanced methods like Quantum encryption can still learn from what has been the past. The allowance of multipath layer security also establishes trust in the network and allows third party vendors the confidence to integrate Lonero with their point of sale systems. Over time, you are establishing a mathematical standard for trust through proof of cryptography for every single new string of nodes created. Just as money used to have a gold standard, cryptocurrency needs to have both a cryptographic and mathematical standard. These topics are highlighted more in our mathematical proofs.
Analyzing Polynomial Time¶
2O(log n) = poly(n) → Karmarkar’s theorem2poly(log n) → Quasi-polynomial time
Karmarkar’s theorem is utilized for solving linear problems in polynomial time. This is where statistical analysis will allow for regression. By utilizing Quasi-Polynomial time, it creates complex sequential rings and patterns for the blockchain’s ring signature. This allows for the ability to create more mathematical proofs for solving a block. Another primary aspect to recursive functions are patterns that fall under the same patterns as Volterra integro-differential equations. This is especially true with sequential data, in which having hybrid mining algorithms typically utilizes a piecewise polynomial within its logic. Since you are analyzing polynomial regression, you can create algorithmic extensions to solving certain aspects of the blockchain such as computational benchmarks and predictive analysis for having a better luck chance of solving the block.
Merkle Mathematical Proofs¶
The Merkle tree proof that we are utilizing is the integration of the ring signature verification, multipath layer security and the utilization of polynomial time. The sequential rings and patterns integrated on the blockchain allow for more efficient hashing and regression for further nodes in the transactional roots. Because of the mathematical proof we have, people can create their own custom mining algorithms to go along with what will be readily available in the market. Later, depending on community support, we may also create open source tools and developer SDKs centered around algorithmic capabilities and PoC mining for end users.
The Ring Signature Protocol¶
We utilize cryptonote’s ring signature protocol for verification of transactional PoW. Traditional methods utilize a public and private key integration for verifying the original signature of a transaction. However, ring signatures add an extra layer of complexity and security. They utilize several public and private keys for the shared transactional hash to verify the block. This means instead of just one public to private key verification, you are further increasing security by adding more signatures to your transactions. Utilizing this group verification method is known as “Ring Signatures” and is similar to the original signature method but integrates multiple signatures for verification. Since you are using multiple signatures, the original transaction root still knows the original public and private signers once the verification for a transaction hash is verified.
In terms of using large scale systems, ring signatures allows for the transactions to be eventually untraceable and a more secure form of exchange. However, methods can still be implemented to prevent abuse of the system. Having, a ring signature type protocol allows for a more open market, and when utilized correctly, you can still have a network with high speeds. Compliance is still possible with advanced forms of exchange and allowing a technological implication of these protocols can make actions such as cross border transactions faster, safer, and significantly more secure.
Problem with Current Mining¶
Traditional mining systems are extremely outdated and inefficient. They require higher capacity hardware for greater profitability, which leads to the opportunity for market monopolies. Market monopolies can hence be created for mining hardware, GPU systems, or even centralized towards people who have data centers or mining farms. While, it is true that people with greater hardware capacity may profit more using traditional mining on Lonero’s systems, there are still ways around it. Creating the ability for “Proof of Capacity” mining solutions, (as talked about earlier), allows for people to solve the blockchain utilizing their mathematical capabilities and understanding. Now, not only wealth is rewarded, but mathematical knowledge.
Applying Euclidean Geometry¶
We have plans to integrate computer vision technologies later with Lonero’s core technological infrastructure. Part of this will be Euclidean geometry and an A.I. that can integrate with merkle tree proofs. This will be integrated in a series of different areas such as the DAO creation, compression on the blockchain, and sequential pattern recognition amongst the network. Imagine a merkle tree being geometrically analyzed and manipulated as is a data structure. Obviously, this will be a long stretch goal in terms of integrating with Lonero’s core development and will be laid out for the community over time.
For more info read Beyond Blockchain: The Futurist Guide to Innovative Technologies or visit the Lonero website.